Global view of example systems, with their overall description, that are represented in this project.
A generic model with generic name that doesn't represent a particular system. Useful to introduce a methodology without leading people into a particular architecture.
A mobile application to manage tenants of an apartment complex and sells various products that the landlord brews and grows. Tenants can use the mobile app to pay rent, buy products and receive fire n' surf alerts.
A desktop application based on Electron that handle cryptocurrency operations with the Blockchain. The model also includes related components such as a Cryptocurrency Exchange web site and a trading bot in python.
A simple web content management system with generic name components. Has a web server, a database and a CDN.
An internet of things device such as a lightbulb that is controlled with a mobile app, a python script or a cloud API. A website provides the cloud integration user interface and the IoT device exposes a local network API.
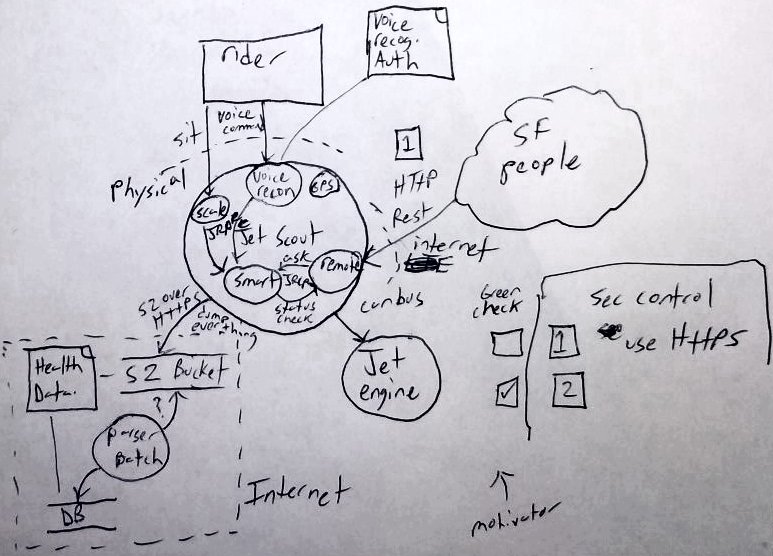
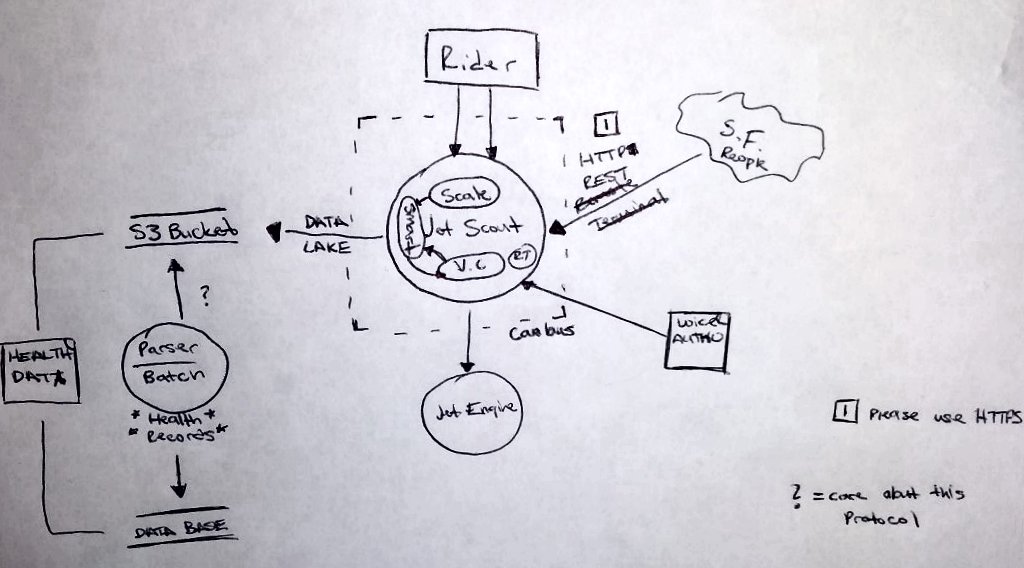
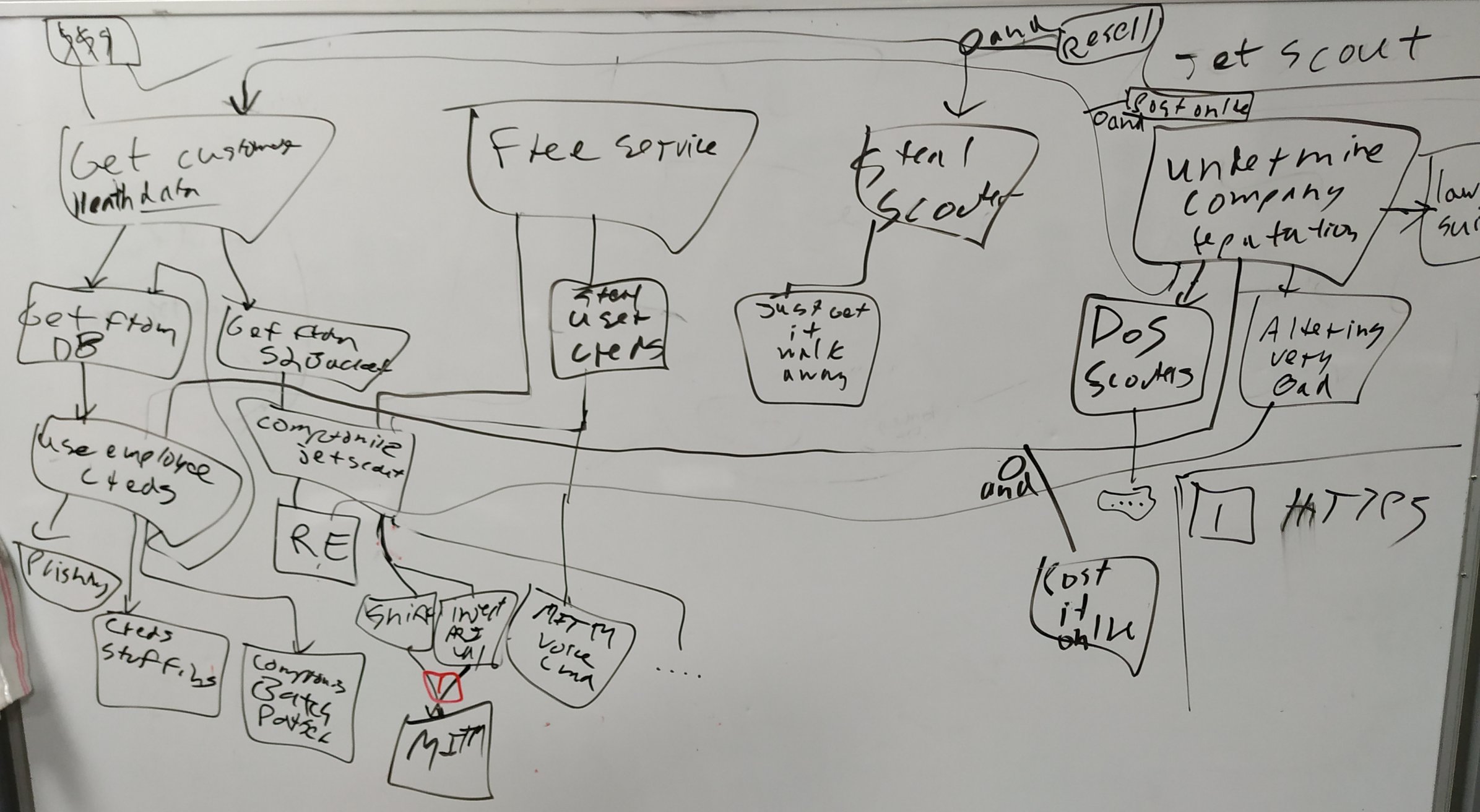
A rental scooter equipped with a jet engine and tracking system that relies on IoT smart components. It receives voice commands and has a seat with a smart scale on it to know when the rider is sitting or has felt. It tracks health data from smart sensors and store it into the cloud for insurance purpose (totally not for reselling it). It has also a remote API that can control its jet engine.
A multiplayer video game client and server that has a lobby for matchmaking and provide statistics about the matches and players. Player accounts are stored in a central database and Customer Support staff can access it for moderation purposes.
A textbook example of a physical safe that a bad actor wants to open.
A startup ecosystem based on mobile applications and APIs that manage peer to peer car rentals. A customer can use a mobile app to unlock and start the car. The owner of the car has its own mobile app to manage rentals. It has AI linked to its APIs and supports augmented reality features. The APIs also allows to change radio stations which are stored in the cloud on a flat file for legacy reasons.
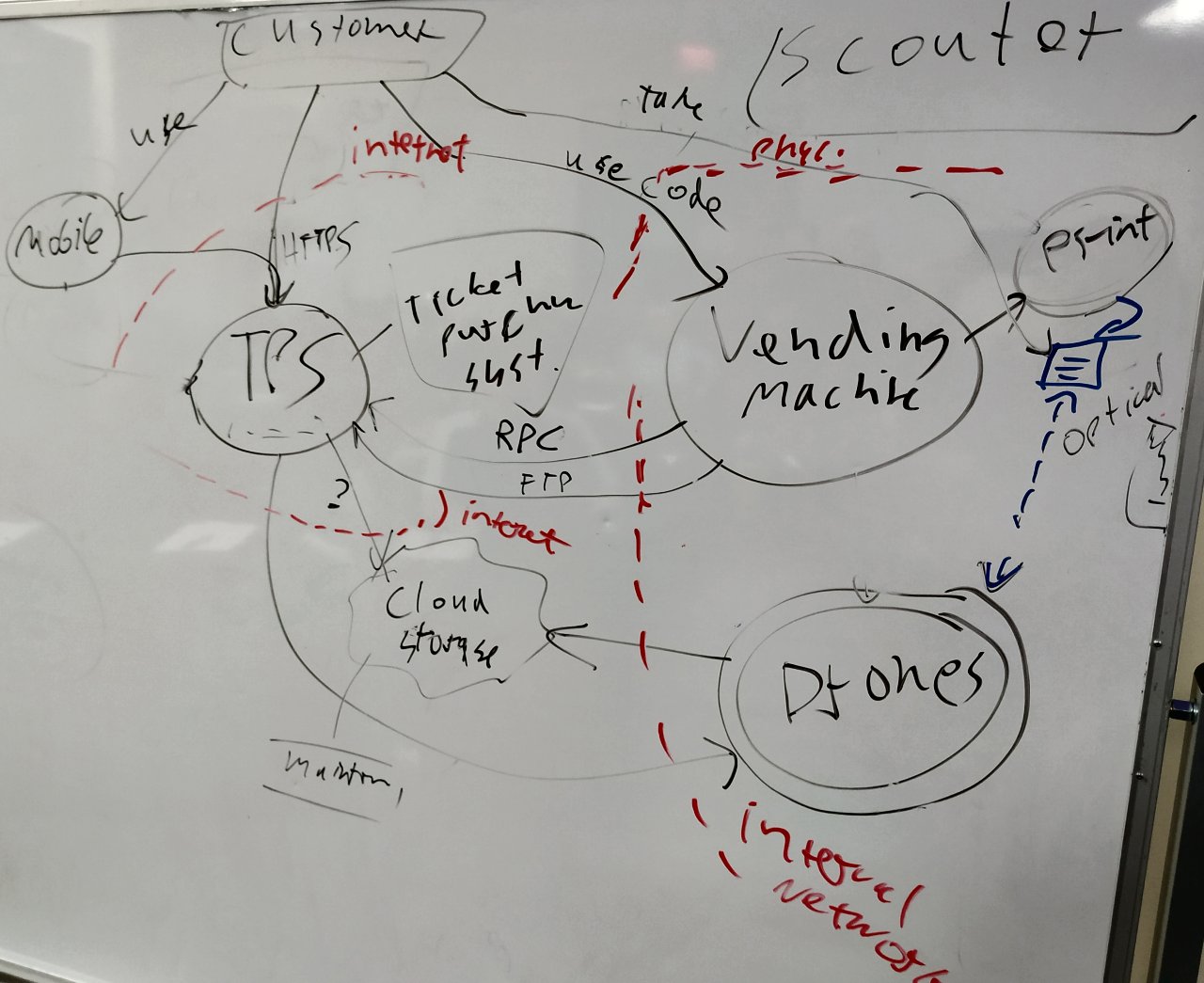
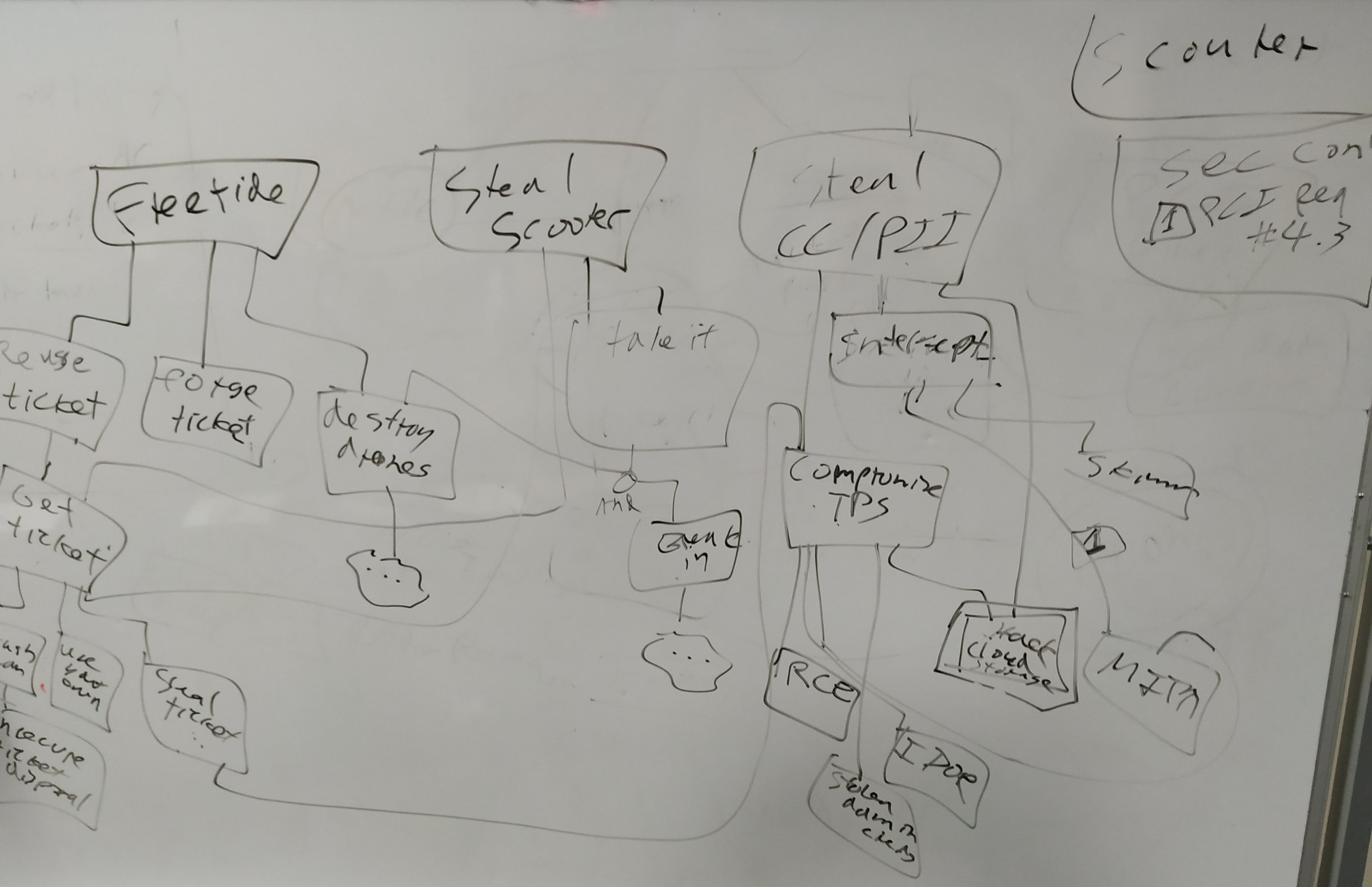
A shared scooter company (competitor of jetscout) that uses a vending machine to distribute tickets for renting their fleet of shared electric scooters. They use drones to track customers.
An online hipster store platform that allows people to see pictures of socks on social medias and buy them. Its main components are a mobile application and an API, which connect to a legacy inventory management system that still sends fax.
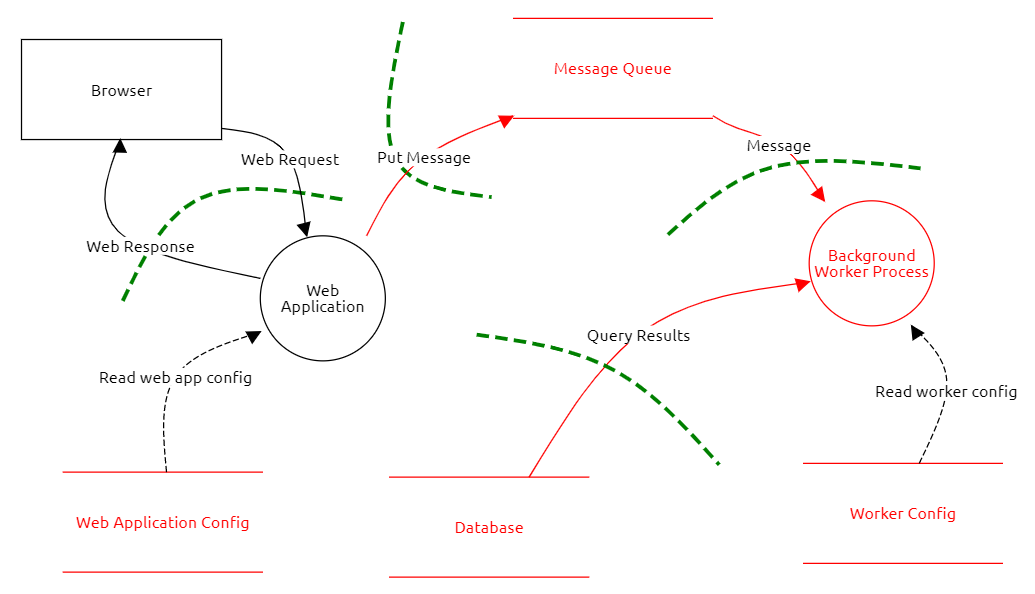
A sample model of a web application, with a queue-decoupled background process. The OWASP Threat Dragon PDF example contains a report with details about elements with a description of threats and theirs mitigation.
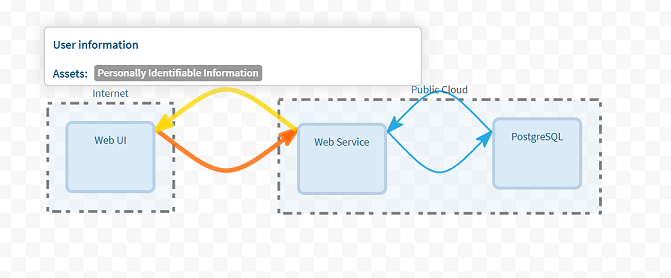
This fictitious application exposes a Web UI on the internet and has a Web API and Database hosted on a public cloud provider. This is a full example using the IriusRisk threat modeling tool from ContinuumSecurity.