You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
The web backend server for GPT-SoVITS lacks proper user input sanitization in the Audio Slicer component, which leads to remote OS command injection vulnerability. This flaw allows attackers to execute arbitrary commands, compromising the system and causing critical security risks.
Due to this vulnerability and the web server's default public exposure, the GPT-SoVITS server is unsuitable for deployment in public production environments until the vulnerability is patched.
Affected Versions
Relased version < 20240821v2
As for today (2024.12.10), all versions of repo code
Details
The vulnerability originates from the open_slice function in the audio slicer component, in which a shell command is constructed using several user-controllable variables.
An attacker can exploit this command injection vulnerability by crafting malicious inputs. These inputs can be provided via the HTML forms or modified in the HTTP request, as highlighted in the screenshot below:
PoC (Proof of Concept)
An attacker can easily achieve remote command execution (RCE) by inserting a malicous payload into any of the parameters in a audio slice operation.
Install and Deploy the GPT-SoVITS following the instruction with WebUI enabled
Summary
The web backend server for
GPT-SoVITSlacks proper user input sanitization in the Audio Slicer component, which leads to remote OS command injection vulnerability. This flaw allows attackers to execute arbitrary commands, compromising the system and causing critical security risks.Due to this vulnerability and the web server's default public exposure, the
GPT-SoVITSserver is unsuitable for deployment in public production environments until the vulnerability is patched.Affected Versions
Relased version < 20240821v2
As for today (2024.12.10), all versions of repo code
Details
The vulnerability originates from the
open_slicefunction in the audio slicer component, in which a shell command is constructed using several user-controllable variables.An attacker can exploit this command injection vulnerability by crafting malicious inputs. These inputs can be provided via the HTML forms or modified in the HTTP request, as highlighted in the screenshot below: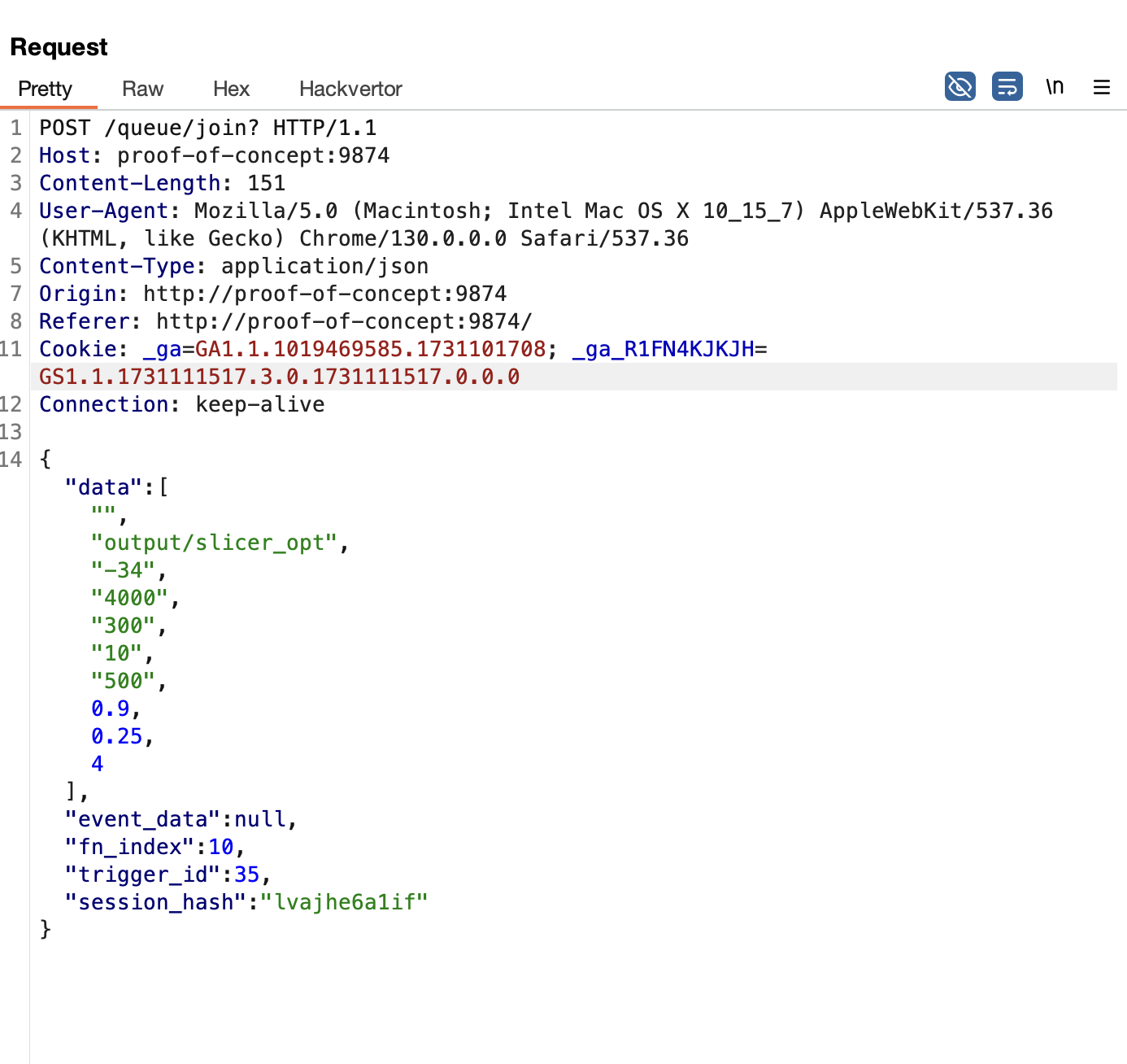
PoC (Proof of Concept)
An attacker can easily achieve remote command execution (RCE) by inserting a malicous payload into any of the parameters in a audio slice operation.
GPT-SoVITSfollowing the instruction with WebUI enabledReplacing cmd value with your desired to trigger an RCE attack:
python SoVITS-audio-slicer-exp.py -u http://proof-of-concept:9874/ -cmd "ping XXX"Patch
To fix the vulnerability:
Avoid using
shell=TrueinPopen.The text was updated successfully, but these errors were encountered: