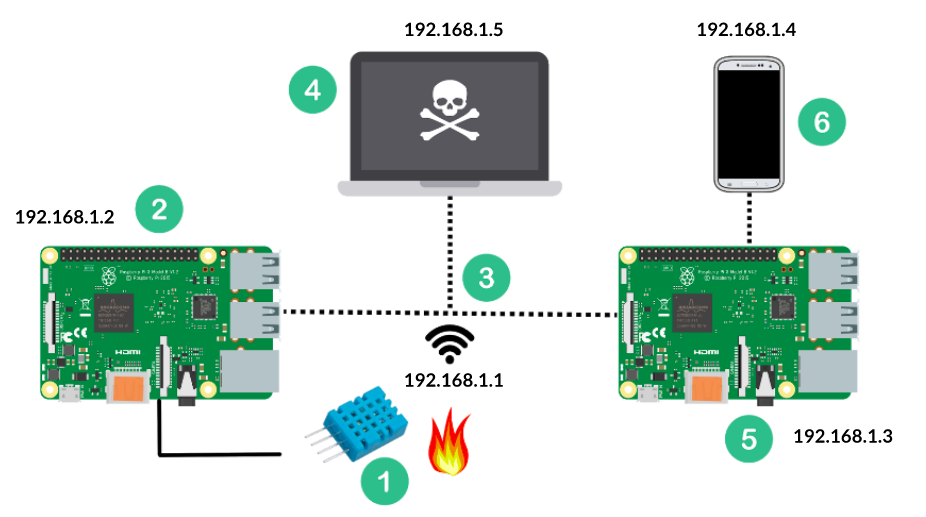
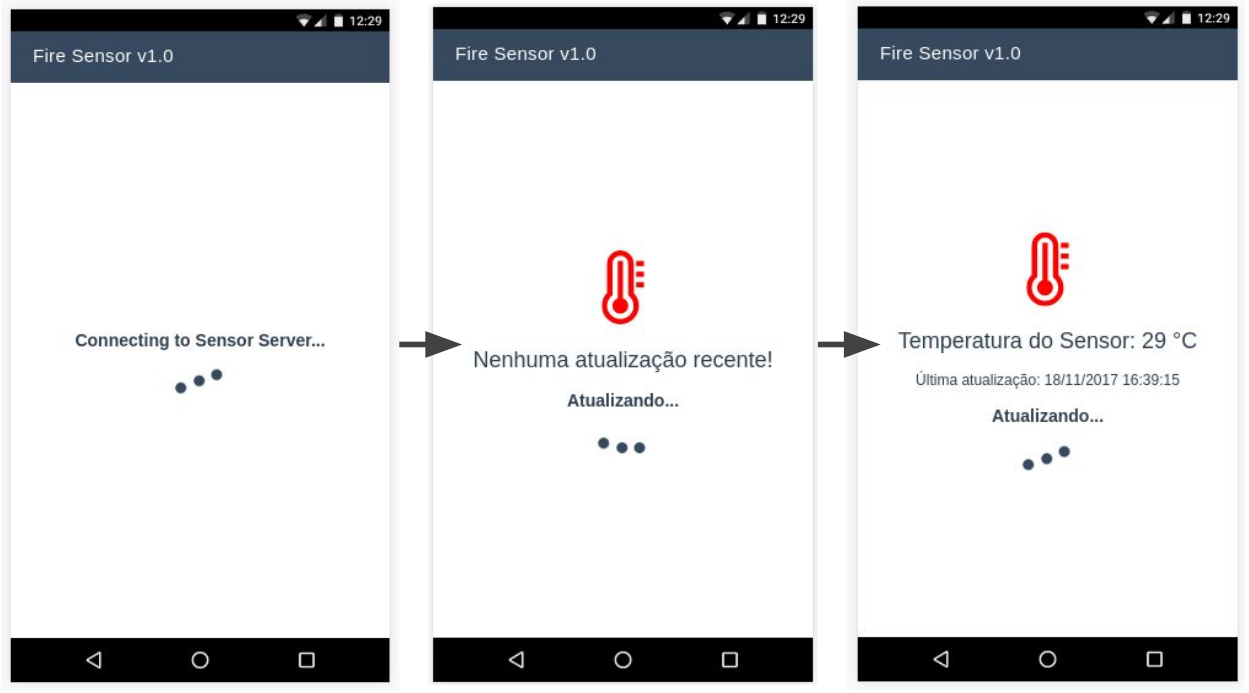
Considering the increase of IoT devices, this work proposes a weakness evaluation in IoT network of devices and possible solutions. This security IoT project uses a DHT11 sensor with Raspberry Pi, showing real-time temperatures in VueJS PWA.
Demo - Loads VueJS PWA with socket connection.
⚠️ Due to Heroku Free One Dyno Plan, this demo can't run HTTP requests and websocket connection together. If you know a way to make this feasible in Heroku Cloud, send a PR or a message.
This project covers an IoT devices network using HTTP transmission between two Raspberry Pi 3 B model, which one of the Rasps collects the sensor temperature and the other one acts like a webserver with Flask to provide the temperature data to a mobile device - developed with VueJS 2 and PWA boilerplate. This way, the user can check if there's a fire with his/her mobile device.
As security will be in check, network transmissions will always have a Darth reading and modifying the collected data. The proposed solution aims to fight Darth (not Vader, but as evil as him) to ensure data integrity and confidentiality through cryptography techniques. This will ensure to the server to identify if the received information was tampered or from a unknown source.
1. Raspberry Client Sensor Server
3. Progressive Web App with VueJS
Flask Deployment on the Heroku Cloud
How to setup the DHT11 Humidity Sensor on the Raspberry Pi
Process Types and the Procfile
Mitmproxy - Modes of Operation
Intercept, Analyze, and Modify Puzzle and Dragons Game Traffic
This work was developed to System Security undergrad-subject final project. The people involved in the project are:
Student: POLETTO, André // polettoandre [at] gmail.com
Student: KAWASAKI, Davi // davishinjik [at] gmail.com
Student: ROZAN, Higor Augusto Bassi // higorb.rozan [at] gmail.com
Student: RODER, Nicholas Ribeiro // nilroder [at] gmail.com
Professor: YOKOYAMA, Roberto Sadao // yokoyama [at] utfpr.edu.br
Feel free to contact or pull request me to any relevant updates you may enquire:
KAWASAKI, Davi // davishinjik [at] gmail.com