-
Notifications
You must be signed in to change notification settings - Fork 0
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[ByteByteGo Daily] Password, Session, Cookie, Token, JWT, SSO, OAuth - Authentication Explained - Part 1 #143
Comments
Authentication waysPassword AuthenticationIn this method, users enter their unique username and password combination to gain access to protected resources
|
HTTP Basic Access Authentication
|
Session-Cookie AuthenticationSession-cookie authentication addresses HTTP basic access authentication's inability to track user login status.
|

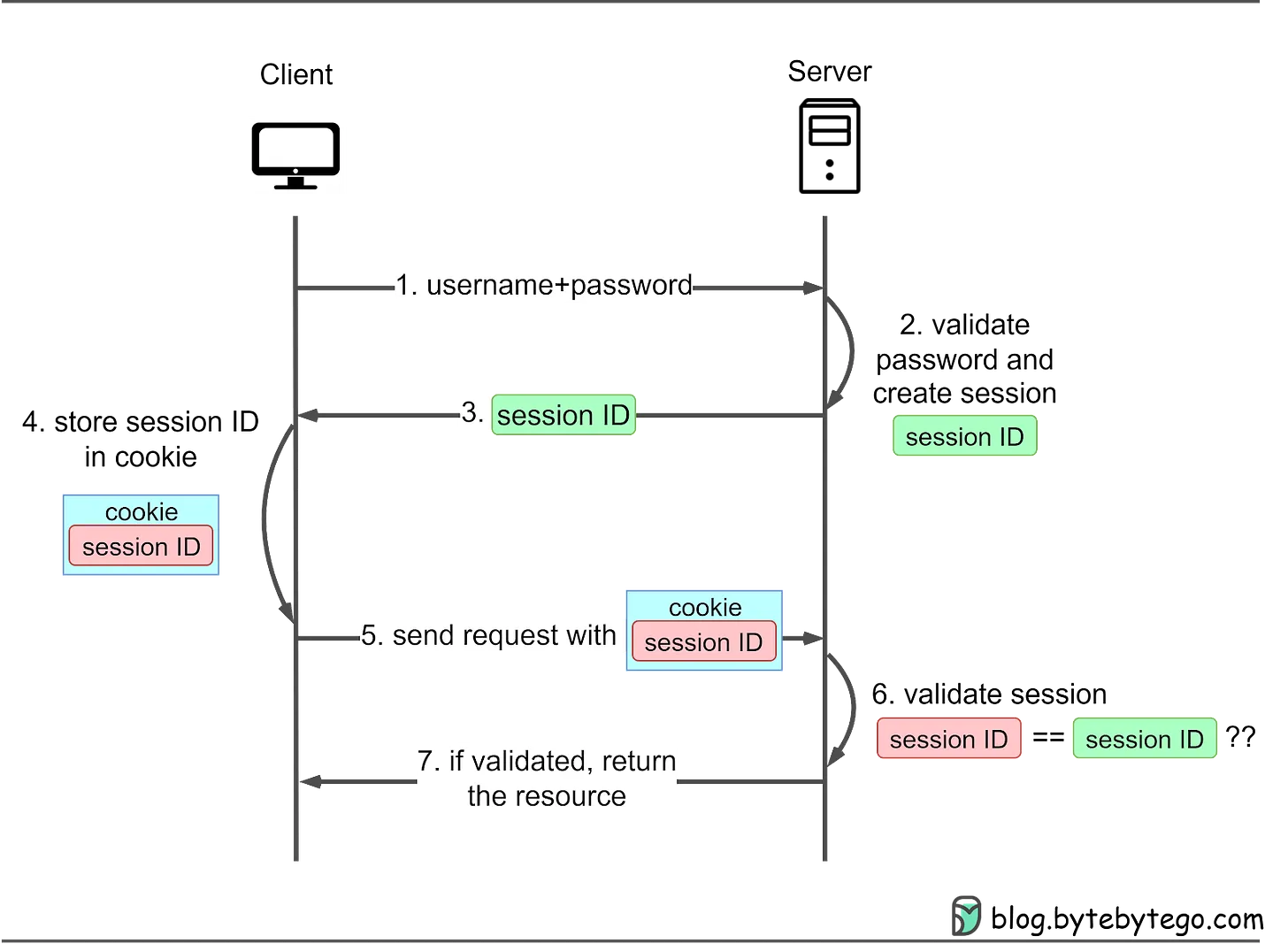
Overview
This notes is extracted from Password, Session, Cookie, Token, JWT, SSO, OAuth - Authentication Explained - Part 1, By Alex Xu
There are three essential security steps when we use various of websites (or applications)
The text was updated successfully, but these errors were encountered: