Goblin is a phishing rehearsal tool for red-blue confrontation. By using a reverse proxy, it is possible to obtain information about a user without affecting the user's operation perceptibly, or to induce the user's operation. The purpose of hiding the server side can also be achieved by using a proxy. Built-in plug-in, through a simple configuration, quickly adjust the content of the web page to achieve a better exercise effect.
📒 中文 README | 📌 Releases Download | 📖 Documents
- Support for caching static files to speed up access.
- Supports dumping all requests, dumping requests that match the rules.
- Support quick configuration through plug-ins to adjust inappropriate jumps or content.
- Support for implanting specific javacript code.
- Support for modifying the content of responses or goblin requests.
- Support hiding real IP by proxy.
Quick Experience
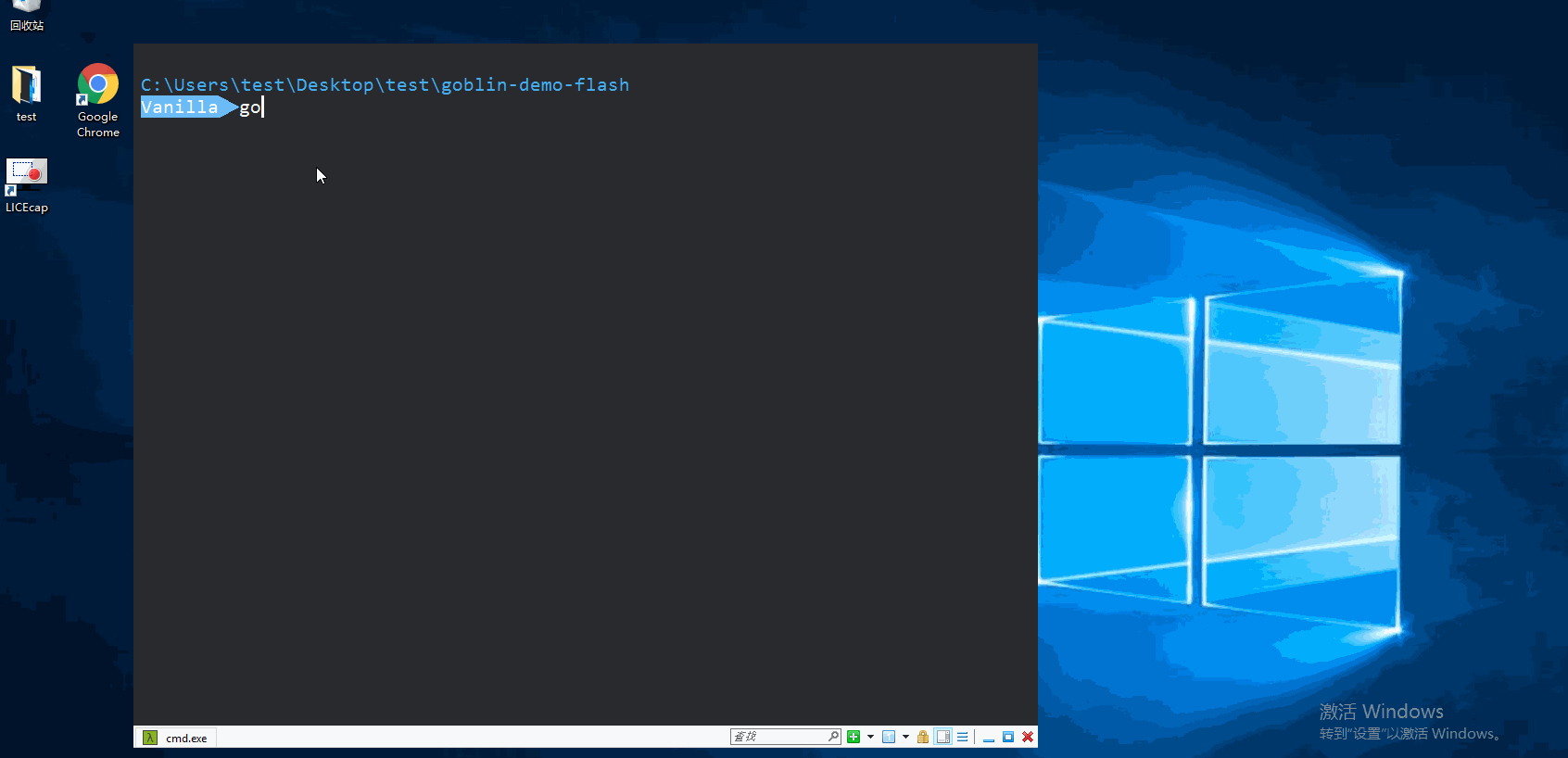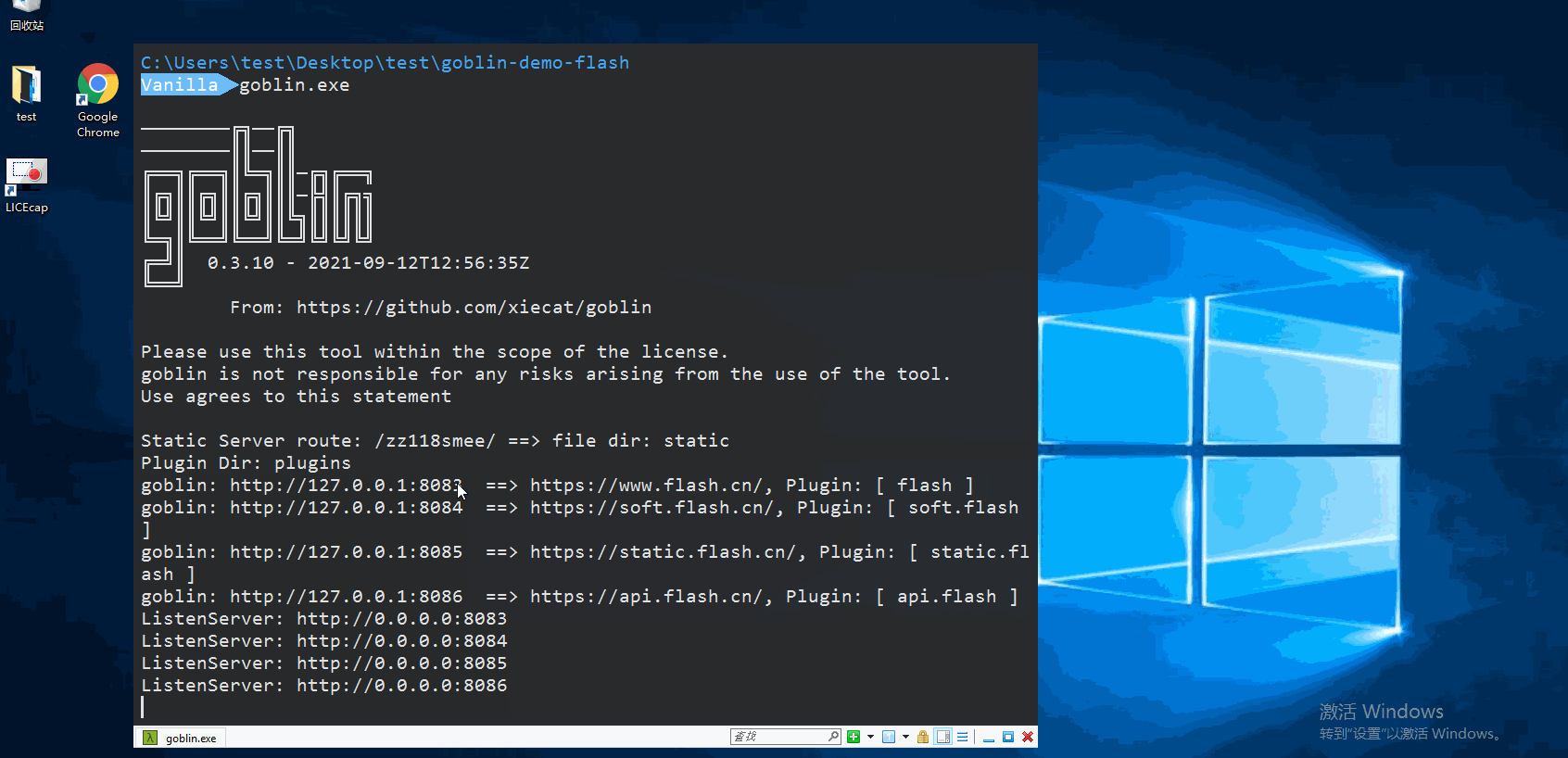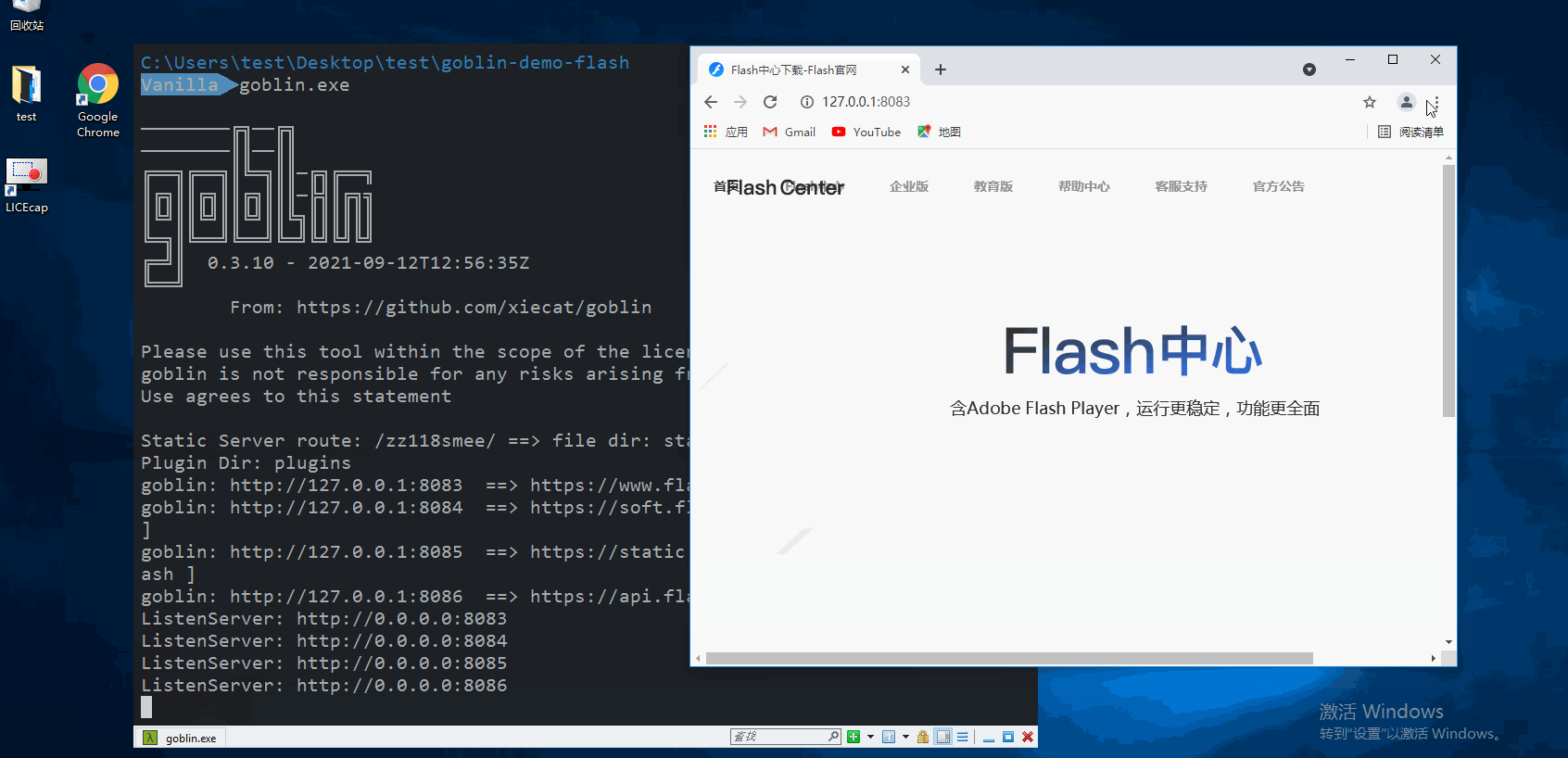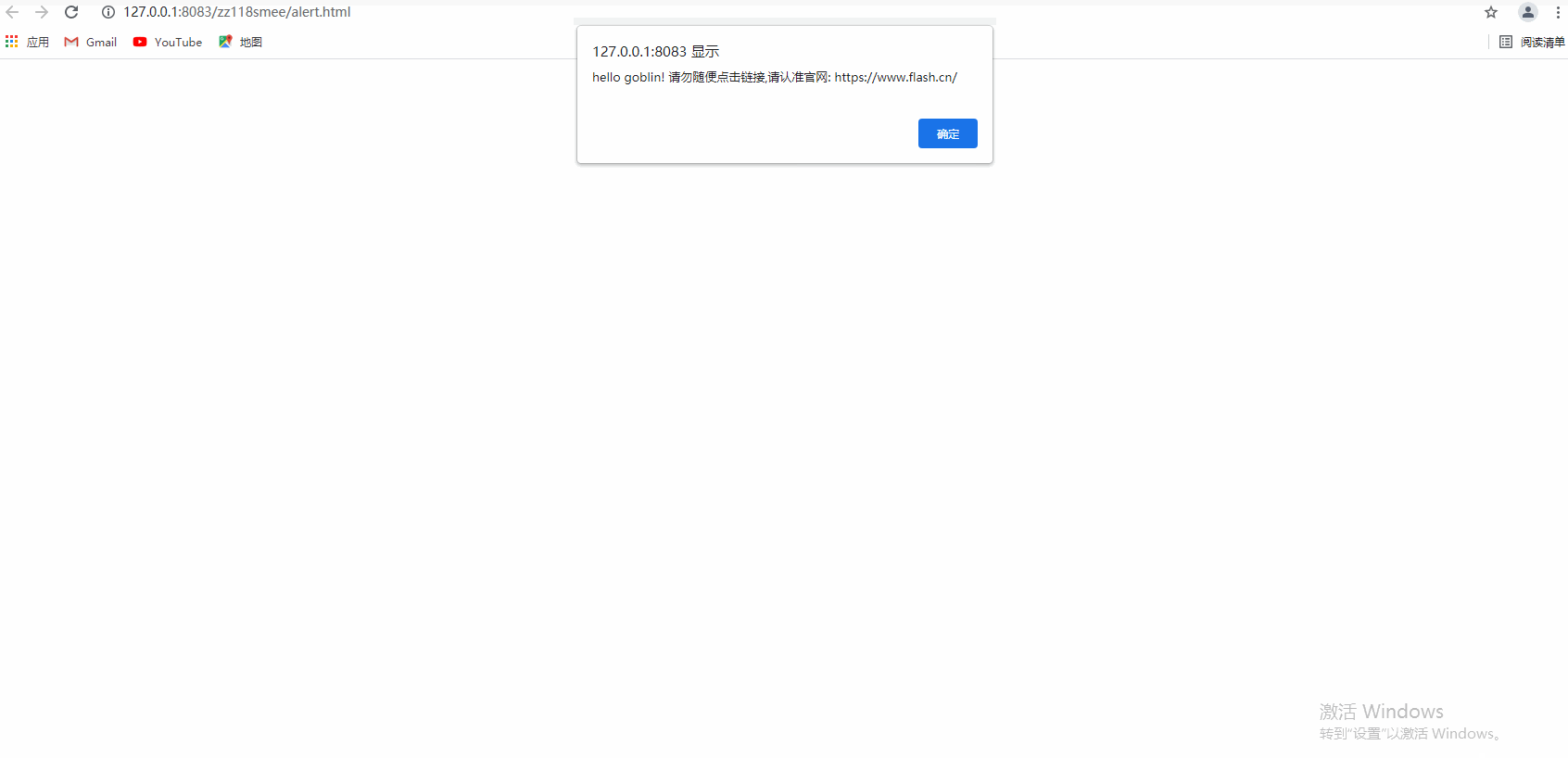
- Proxy Flash.cn
docker run -it --rm -p 8083:8083 -p 8084:8084 -p 8085:8085 -p 8086:8086 becivells/goblin-demo-flashAccess to http://127.0.0.1:8083, corresponding example repo: goblin-flash-demo.
- Proxy Baidu.com
docker run -it --rm -v $(pwd):/goblin/ -p 8084:8084 becivells/goblinAccess to http://127.0.0.1:8084.
Run the following command to pull the image.
docker pull becivells/goblinDockerfile:
FROM scratch
COPY goblin /usr/bin/goblin
ENTRYPOINT ["/usr/bin/goblin"]
WORKDIR /goblinThe working directory is in goblin, first create the directory, go to the directory and execute the following command.
docker run -it --rm -v $(pwd):/goblin/ -p 8084:8084 becivells/goblin-
Visit releases to select the appropriate binary for your operating system from there.
-
Modify the parameters of the configuration file according to your needs. For details of the configuration file, please refer to the usage documentation 👉 Introduction to the configuration file.
Command-line arguments:
Usage of goblin:
-config string
Webserver port (default "goblin.yaml")
-gen-plugin string
Generate rule file
-log string
Webserver log file (default "goblin.log")
-log-level int
Log mode [1-5] 1.dump All logs include GET log and POST log, 2. Record POST log, 3. Record dump log in rules, 4. Record error log, and 5. Record exception exit log (default 2)
-print-config
print config file
-test-notice
Test message alarm
-v Show version of goblin
-w Write config to config fileIf the server-side deployment requires changing the ip address. if you have any questions, please refer to the site explanation.
Site:
server_ip:8084: ## Change to domain name or server IP
Listen: 0.0.0.0
StaticPrefix: x9ut17jbqa
SSL: false
CAKey: ""
CACert: ""
ProxyPass: https://www.baidu.com
Plugin: demoSee documentation for introduction details and usage 👉 Plug-in system.
goblin uses a reverse proxy. The frontend uses a proxy such as cloudflare goblin, that can hide the goblin host. Documentation details can be found in the goblin proxy configuration.
There are two ways to inject javascript: one is to follow the page (Replace requires you to append \<script\> tags), and the other is to follow the global js file, each approach has its own benefits.
Both of these actually use the Replace function.
For details, please refer to goblin InjectJs module.
- url: /base.js # JS to be replaced, with preference for global JS.
Match: word # Matching method.
InjectJs:
File: aaa.js # The JS to be replaced, it can be a file or a url.For details, please refer to goblin Replace module.
- url: /art_103.html # Pages to be replaced.
Match: Word
Replace: # Replacement Module.
- Request:
Method: # Match to the following request method before replacement.
- GET
- POST
Header:
goblin: 1.0.1 # Replace the header content. If empty, it is deleted.
Response: # Replacement response content.
Body:
Append: "<script type='text/javascript' src='{{ .Static }}a.js'></script>" # Append string.For more cases, please enter the Discord group for discussion, or submit an issue.
- Front-end record input box input.
Thanks to Master(小明)'s use, feedback and suggestions, and _0xf4n9x_'s suggestions. judas brought inspiration, and references to other projects, to enable quick implementation.
You can submit an issue.
In the meantime, you can join our Discord discussion group.
This tool can only be used in enterprise security construction and offensive and defensive exercises with sufficient legal authorization. In the process of using this tool, you should ensure that all your actions comply with local laws and regulations. If you have any illegal behavior in the process of using this tool, you will bear all the consequences by yourself, and all developers and all contributors of this tool will not bear any legal and joint liability. Please do not install and use this tool unless you have fully read, fully understood and accepted all the terms of this agreement. You are deemed to have read and agreed to be bound by this Agreement by your act of use or by your acceptance of this Agreement in any other way, express or implied.