This Simple DNS Honeypot Server is a streamlined script designed for cybersecurity enthusiasts and professionals. This Python script, leveraging the Twisted framework, establishes a low-interaction DNS server to log and monitor DNS queries. It serves as an essential instrument for basic network traffic analysis and early detection of potential security threats, making it perfect for entry-level cybersecurity practice and threat awareness.
- Low-Interaction Honeypot: Minimizes complexity and reduces risk.
- Customizable DNS Server: Host and port settings are easily configurable.
- Comprehensive Logging: Captures DNS query details for analysis.
- Real-time Monitoring: Instantly logs DNS queries for security monitoring.
- Security Research Tool: Excellent for understanding DNS-based threats and network probing.
- Python 3.x
- Twisted Python library
Clone the repository or download the dns.py script. Ensure Python and Twisted are installed.
git clone https://github.com/0xNslabs/dns-honeypot
cd dns-honeypot
pip install twistedExecute the script with optional arguments for host and port. Defaults to 0.0.0.0 (all interfaces) and port 5353.
python3 dns.py --host 0.0.0.0 --port 5353Logs are stored in dns_honeypot.log, detailing each DNS query received by the server for further scrutiny.
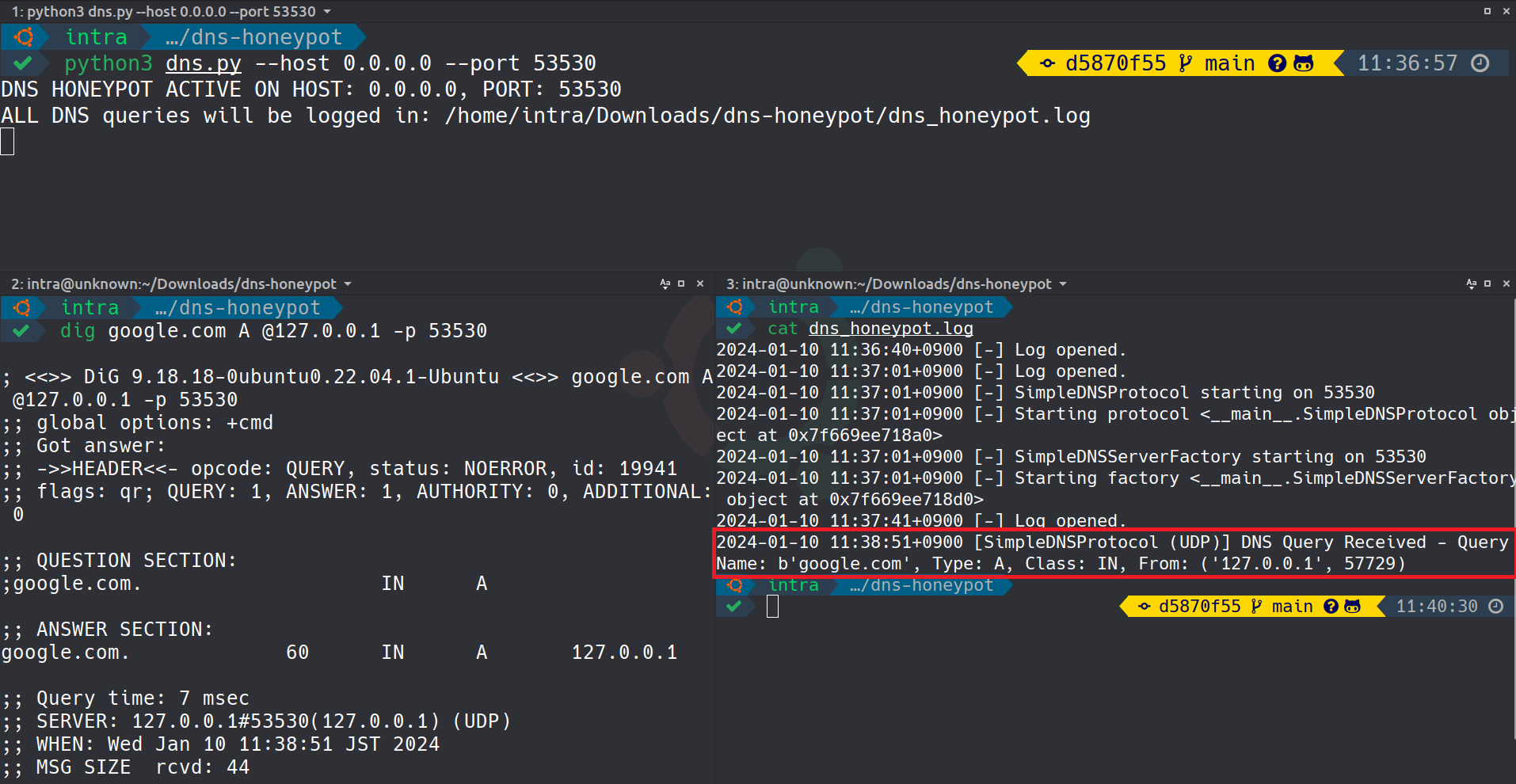 The image above captures the Simple DNS Honeypot logging real-time DNS queries
The image above captures the Simple DNS Honeypot logging real-time DNS queries
Check out the other honeypot services for monitoring various network protocols:
- DNS Honeypot - Monitors DNS interactions.
- FTP Honeypot - Simulates an FTP server.
- LDAP Honeypot - Mimics an LDAP server.
- HTTP Honeypot - Monitors HTTP interactions.
- HTTPS Honeypot - Monitors HTTPS interactions.
- NTP Honeypot - Monitors Network Time Protocol interactions.
- PostgreSQL Honeypot - Simulates a PostgreSQL database server.
- SIP Honeypot - Monitors SIP (Session Initiation Protocol) interactions.
- SSH Honeypot - Emulates an SSH server.
- TELNET Honeypot - Simulates a TELNET server.
- Caution: This server is a honeypot. Employ responsibly in controlled network environments.
- Compliance: Adhere to local laws and regulations in deployment.
This project is distributed under the MIT License. See LICENSE for more information.