- Introduction
- Usage
- GUI
- Requirements
- Installation
- Extended Usage
- Configuration
- Features
- Contributing
- Documentation
- Troubleshooting
- License
- Credits
- Changelog
- Roadmap
- Demos
- Funding
Slips is a powerful endpoint behavioral intrusion prevention and detection system that uses machine learning to detect malicious behaviors in network traffic. Slips can work with network traffic in real-time, PCAP files, and network flows from popular tools like Suricata, Zeek/Bro, and Argus. Slips threat detection is based on a combination of machine learning models trained to detect malicious behaviors, 40+ threat intelligence feeds, and expert heuristics. Slips gathers evidence of malicious behavior and uses extensively trained thresholds to trigger alerts when enough evidence is accumulated.
Slips is the first free software behavioral machine learning-based IDS/IPS for endpoints. It was created in 2012 by Sebastian Garcia at the Stratosphere Laboratory, AIC, FEE, Czech Technical University in Prague. The goal was to offer a local IDS/IPS that leverages machine learning to detect network attacks using behavioral analysis.
Slips is supported on Linux and MacOS only. The blocking features of Slips are only supported on Linux
Slips is Python-based and relies on Zeek network analysis framework for capturing live traffic and analyzing PCAPs. and relies on Redis >= 7.0.4 for interprocess communication.
The recommended way to use Slips is on Docker.
docker run --rm -it -p 55000:55000 --cpu-shares "700" --memory="8g" --memory-swap="8g" --net=host --cap-add=NET_ADMIN --name slips stratosphereips/slips:latest
./slips.py -f dataset/test7-malicious.pcap -o output_dir
cat output_dir/alerts.log
docker run --rm -it -p 55000:55000 --cpu-shares "700" --memory="8g" --memory-swap="8g" --net=host --cap-add=NET_ADMIN --name slips stratosphereips/slips_macos_m1:latest
./slips.py -f dataset/test7-malicious.pcap -o output_dir
cat output_dir/alerts.log
docker run --rm -it -p 55000:55000 --cpu-shares "700" --memory="8g" --memory-swap="8g" --net=host --cap-add=NET_ADMIN --name slips stratosphereips/slips:latest
./slips.py -f dataset/test7-malicious.pcap -o output_dir
cat output_dir/alerts.log
For a detailed explanation of Slips parameters
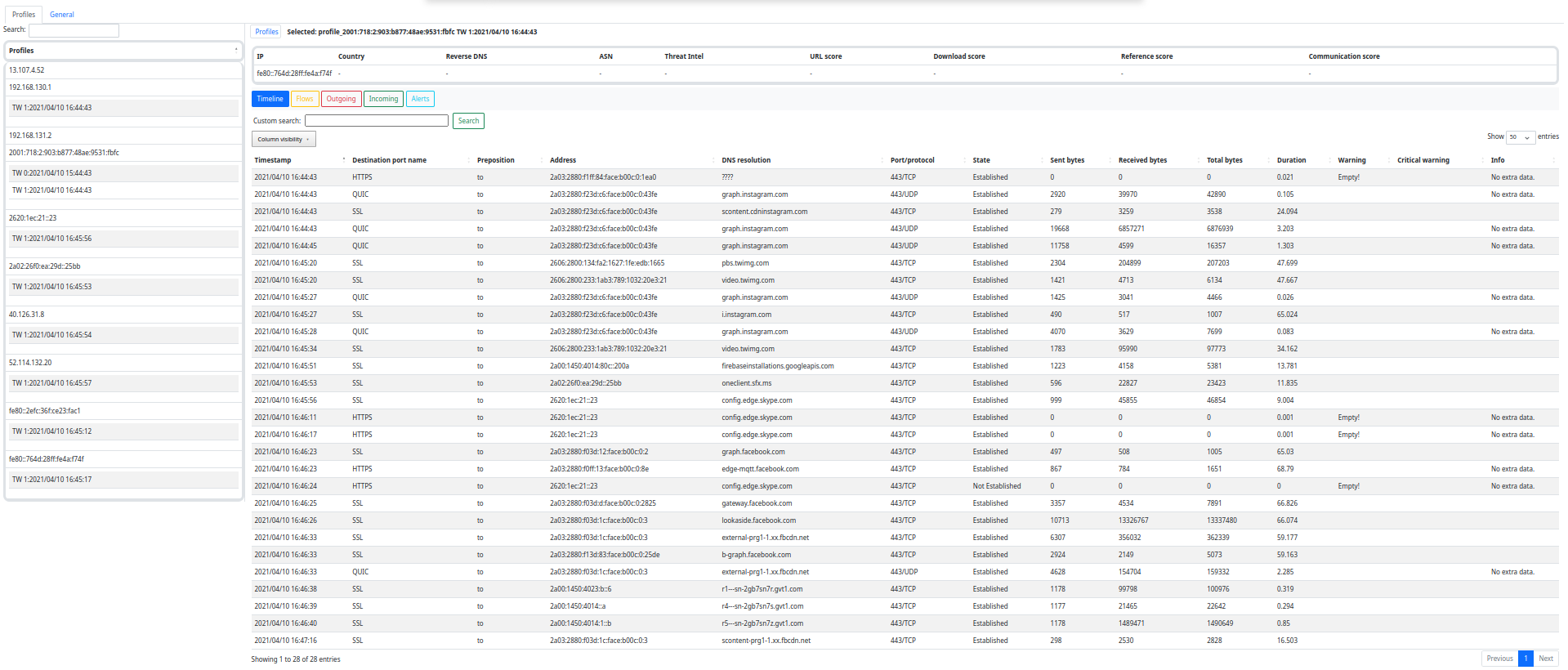
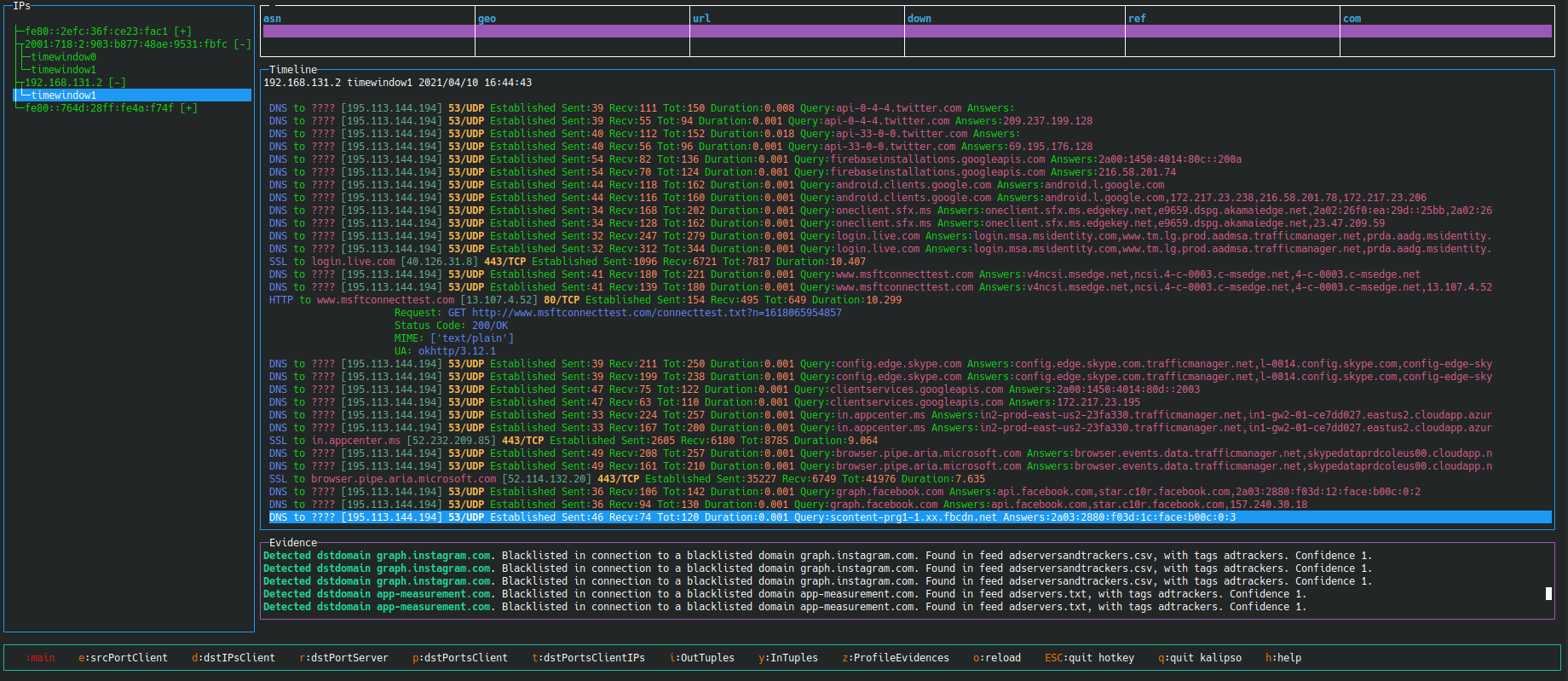
To check Slips output using a GUI you can use the web interface or our command-line based interface Kalipso
./webinterface.sh
Then navigate to http://localhost:55000/ from your browser.
For more info about the web interface, check the docs: https://stratospherelinuxips.readthedocs.io/en/develop/usage.html#the-web-interface
./kalipso.sh
For more info about the Kalipso interface, check the docs: https://stratospherelinuxips.readthedocs.io/en/develop/usage.html#kalipso
Slips requires Python 3.8+ and at least 4 GBs of RAM to run smoothly.
Slips can be run on different platforms, the easiest and most recommended way if you're a Linux user is to run Slips on Docker.
- Docker
- Dockerhub (recommended)
- On a linux host
- On MacOS M1 host
- On MacOS Intel processor
- Docker-compose
- Dockerfile
- Dockerhub (recommended)
- Native
- on RPI (Beta)
Slips has a config/slips.conf that contains user configurations for different modules and general execution.
-
You can change the timewindow width by modifying the
time_window_widthparameter -
You can change the analysis direction to
allif you want to see the attacks from and to your computer -
You can also specify whether to
trainortestthe ML models -
You can enable popup notifications of evidence, enable blocking, plug in your own zeek script and more.
More details about the config file options here
Slips key features are:
- Behavioral Intrusion Prevention: Slips acts as a powerful system to prevent intrusions based on detecting malicious behaviors in network traffic using machine learning.
- Modularity: Slips is written in Python and is highly modular with different modules performing specific detections in the network traffic.
- Targeted Attacks and Command & Control Detection: It places a strong emphasis on identifying targeted attacks and command and control channels in network traffic.
- Traffic Analysis Flexibility: Slips can analyze network traffic in real-time, PCAP files, and network flows from popular tools like Suricata, Zeek/Bro, and Argus.
- Threat Intelligence Updates: Slips continuously updates threat intelligence files and databases, providing relevant detections as updates occur.
- Integration with External Platforms: Modules in Slips can look up IP addresses on external platforms such as VirusTotal and RiskIQ.
- Graphical User Interface: Slips provides a console graphical user interface (Kalipso) and a web interface for displaying detection with graphs and tables.
- Peer-to-Peer (P2P) Module: Slips includes a complex automatic system to find other peers in the network and share IoC data automatically in a balanced, trusted manner. The P2P module can be enabled as needed.
- Docker Implementation: Running Slips through Docker on Linux systems is simplified, allowing real-time traffic analysis.
- Detailed Documentation: Slips provides detailed documentation guiding users through usage instructions for efficient utilization of its features.
We welcome contributions to improve the functionality and features of Slips.
Please read carefully the contributing guidelines for contributing to the development of Slips
You can run Slips and report bugs, make feature requests, and suggest ideas, open a pull request with a solved GitHub issue and new feature, or open a pull request with a new detection module.
The instructions to create a new detection module along with a template here.
If you are a student, we encourage you to apply for the Google Summer of Code program that we participate in as a hosting organization.
Check Slips in GSoC2023 for more information.
You can join our conversations in Discord for questions and discussions. We appreciate your contributions and thank you for helping to improve Slips!
If you can't listen to an interface without sudo, you can run the following command to let any user use Zeek to listen to an interface not just root.
sudo setcap cap_net_raw,cap_net_admin=eip /<path-to-zeek-bin/zeek
You can join our conversations in Discord for questions and discussions.
Or email us at
Founder: Sebastian Garcia, sebastian.garcia@agents.fel.cvut.cz, eldraco@gmail.com.
Main authors: Sebastian Garcia, Alya Gomaa, Kamila Babayeva
Contributors:
- Veronica Valeros
- Frantisek Strasak
- Dita Hollmannova
- Ondrej Lukas
- Elaheh Biglar Beigi
- Martin Řepa
- arkamar
- Maria Rigaki
- Lukas Forst
- Daniel Yang
https://github.com/stratosphereips/StratosphereLinuxIPS/blob/develop/CHANGELOG.md
The following videos contain demos of Slips in action in various events:
- 2022 BlackHat Europe Arsenal, Slips: A Machine-Learning Based, Free-Software, Network Intrusion Prevention System [web]
- 2022 BlackHat USA Arsenal, Slips: A Machine-Learning Based, Free-Software, Network Intrusion Prevention System [web]
- 2021 BlackHat Europe Arsenal, Slips: A Machine-Learning Based, Free-Software, Network Intrusion Prevention System [slides] [web]
- 2021 BlackHat USA Arsenal, Slips: A Machine-Learning Based, Free-Software, Network Intrusion Prevention System [web]
- 2021 BlackHat Asia Arsenal, Slips: A Machine-Learning Based, Free-Software, Network Intrusion Prevention System [web]
- 2020 Hack In The Box CyberWeek, Android RATs Detection With A Machine Learning-Based Python IDS [video]
- 2019 OpenAlt, Fantastic Attacks and How Kalipso can Find Them [video]
- 2016 Ekoparty, Stratosphere IPS. The free machine learning malware detection [video]
We are grateful for the generous support and funding provided by the following organizations:
- NlNet Foundation, https://nlnet.nl/
This project is funded through NGI0 Entrust, a fund established by NLnet with financial support from the European Commission's Next Generation Internet program. Learn more at the NLnet project page.
- Artificial Intelligence Centre at the Czech Technical University in Prague, https://www.aic.fel.cvut.cz/
- Avast, https://www.avast.com/
- CESNET, https://www.cesnet.cz/
- Google Summer of Code (2023, 2024), https://summerofcode.withgoogle.com/
Their funding has played a crucial role in the development and success of this project. We sincerely appreciate their commitment to advancing technology and their recognition of the value Slips brings to the community.